Introduction
Key Takeaways

Updated 12/16/19
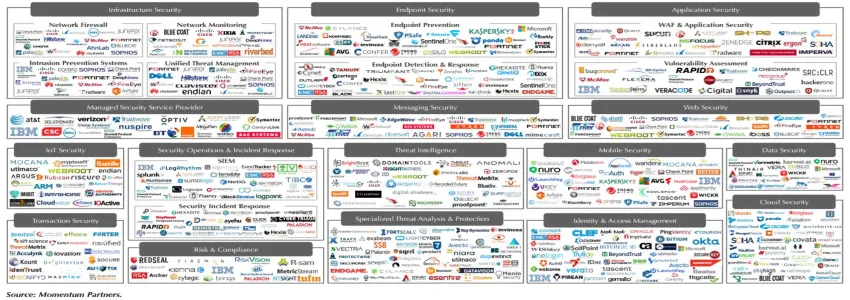
The Current State: Vendor Saturation
I attended the RSA Conference not long ago and had one big takeaway: there are too many cybersecurity vendors. Vendor saturation is one of the biggest challenges currently plaguing the cybersecurity market, according to a recent ZDNet article. Security System Engineer Ronny Guillaume of Cisco Systems stated that organizations are bombarded by too much noise to actually understand what it is they need to protect their business.
"Studies have shown that companies have up to 70 different security vendors installed in their company to solve problems," he said. "Now imagine if you had to go and look at 70 different security products and understand what's going on within your specific environment—it's almost impossible."
The former Chairman of RSA, Art Coviello, agrees and added in this article, “When CISOs seek security technology to solve a specific problem they are faced with 1,500 vendors and the problem is almost insurmountable.”
The explosive growth and subsequent confusion with thousands of vendors can partly be blamed on venture capital—2017 alone saw VCs pump over $6.7 Billion into cybersecurity companies, double that of 2016. This means CIOs and CISOs are getting constantly bombarded by thousands of cybersecurity companies with confusing messages and misunderstood value propositions.
The bottom line is this: there is no shortage of technology to prevent threats; there is a lack of organizing people, process, technology and vendors in an easy way to manage a cohesive cybersecurity program.
First Things First - Why are There so Many Vendors?
We’ve already discussed the venture capital influx, which is largely responsible for the spike in vendor numbers, but what are the other factors at play? According to Ned Miller in a recent McAfee article:
More than 1,200 vendors compete in the cybersecurity market today. Conservatively, if each vendor offers an average of three products, with each product carrying an average of five features, that would make the cybersecurity market replete with nearly 20,000 features.
So what gives? What’s the cause behind this explosion of vendors offering services? Many cybersecurity experts, it’s the actual security that’s playing a big role. Here are some modern security stats to underline this point:
- Between January 1, 2005 and April 18, 2018, there were 8,854 recorded breaches. Together, these breaches affected millions of records, and the price per record ranged from about $120-$600, which places the total price of these breaches is in billions of dollars. While decision-makers like to talk about the cost of installing cybersecurity measures, they seldom talk about how much not having it can cost.
- In 2017, 61% of data breaches targeted companies with less than 1,000 employees. When it comes to cybersecurity, small businesses are a major target. This has more to do with the fact that major companies typically have large security budgets than smaller companies. As such, they're more vulnerable to cyber security threats than larger brands. While it may seem like hackers don’t benefit as much from attacking small companies, the truth is that these small-scale attacks are easier to complete and get away with.
- Around 50% of the risk companies face is due to having multiple security vendors. As if you needed to be more aware of the problem that is vendor saturation. Today, having multiple security vendors is more than just inconvenient - it can actually place a company at risk of security breaches. While it may seem like “the more the merrier” applies to cybersecurity, having multiple security vendors only complicates the security infrastructure and creates more vulnerabilities. Instead, it’s smart to choose a single vendor to cover all your bases.
- In 2017, IoT attacks jumped by 600%. We live in the BYOD (bring your own device) world. In a day and age where virtually everyone has a smartphone, hackers and cybercriminals have more targets than ever before. As IoT devices continue to saturate the market, security struggles to keep up.
As you can see, the security landscape has changed hugely, and the rise in threats and attacks reasonably leads to a spike in vendors. According to TechCrunch:
The global cybersecurity market is booming: Cybersecurity-related spending is on track to surpass $133 billion in 2022, and the market has grown more than 30x in 13 years...Organizations are increasingly investing in cybersecurity, as evidenced by a recent report by Gartner Group showing security spending is outpacing IT spending. Security departments are expanding in size and budget, and, at the helm, security decision-makers are gaining respect more than ever before. With ever-dynamic cybersecurity risks and regulations, it is clear to most C-suite leaders that there’s more to be protected and more on the line.
While the influx of choices is positive for people who need enhanced security, having too many vendors to choose from can also be a very confusing state of affairs.
5 Ways to Sort Through Vendors
Not sure where to start on finding the right vendor for you? You’re not alone. In fact, many merchants struggle to find the ideal security vendor, or to pare down the vendors they currently have. Fortunately, we've compiled five tactics to help you sort through the options and find a solution that fits your needs.
1. Create an inventory of tools you’re currently using
What gets measured gets managed, and this is just as true for your cybersecurity tools as it is anything else. With this in mind, the first step to choosing the right vendor ris to catalog the tools you currently use.
Once you’re able to catalog all of the platforms your team uses and what problem each one solves, you can remove redundant tools that cost you time and money. You can then create a tools coverage map to determine the gaps where you have opportunities for more coverage.
Even if the vendor you're interested in providers services that one of your tools already offers, cataloging the assortment of tools you’re currently using will allow you to compare and contrast. Does your current solution works well enough for your company, or could a new technology support you more efficiently? This is an important compare-and-contrast step that you can’t afford to overlook.
2. Avoid solutions that only address points
If a tool only addresses a small part of your problem, it’s time to think bigger. You should choose products that not only address multiple “points”, but also ones that provide you with a single pane-of-glass that can automate management and reporting. This approach serves two purposes: not only does it keep you from accumulating dozens of vendors - none of whom truly address your needs, but it also ensures better service for your entire team, for the long-term.
Spend some time being discerning about your solutions now, and you’ll be able to sit back and enjoy them later. No matter what you do, the following are critical security services to consider for your company:
- Network security
- Application security
- Ransomware defense
- Device management
- Endpoint security
- Virtual Private Network (VPN)
- Password management
- Malware defense
- Anti-virus
- Firewalls
- Data storage
- Website protection
While it’s okay if a vendor doesn’t offer all these services, their offering should be comprehensive enough to cater to your company’s needs. If there are major gaps left over, consider choosing a different company, instead.
3. Be wary of the “we can do that” mentality
Occasionally, you’ll come across a company that has a real “we can do it” mentality. While there's nothing wrong with being a go-getter, these companies are generally not experts at whatever service they’re adding on at the last moment. If you take them up on these offers, you’ll typically find yourself playing the role of guinea pig on your project - not a place most companies want to be.
If you’re concerned about the quality of your services, consider avoiding ad-hoc agencies for teams that offer custom solutions, instead.
Today, cybersecurity agencies and MSPs like providing packaged services that they can manage and deploy easily, but the best firms will take it one step further - they’ll have the ability to design and build custom solutions that cater to your company’s unique needs. To find the right custom solution for ou, look for a team who understands the risk-based nature of security, and that one size definitely does not fit all. Ideally, you’ll get a plan and strategy that details how the team plans to secure your company.
The right mix of technologies should support your company’s needs and provide a security approach that both responds to and prevents threats, without requiring the company in question to over-extend itself.
4. Read company reviews
Sites like Capterra provide third-party reviews penned by actual customers that have used the product in a real-world setting. If a company provides their name in the review, consider reaching out to the contact to understand how they've implemented the product and any pitfalls they have perceived. In addition to reading the review, you’ll also want to consider what types of clients the MSP has worked with in the past.
The best MSPs have customers across various industries, which illustrates a mastery of the service and the duties therein. Keep in mind, though, that the MSP should be familiar with your specific needs, and that it’s perfectly acceptable to press theme for details or examples of similar companies they’ve worked with in the past. When they provide you with those examples, evaluate them to see how they've managed to help companies in similar industries with similar security needs.
If you happen to come across a company with a large assortment of negative reviews, be wary .This illustrates some lack of expertise or pattern of poor customer service.
5. Consider Scalability
Any security solution you invest in should grow with your company. Because of this, it’s wise to consider the likelihood of scalability before you buy your new solution. For best results, look for security companies that offer a menu of services or a widespread portfolio of services.
--
Ideally, the company that you eventually choose should have the tools and equipment to serve your entire organization. Before you choose a vendor, consider how you plan to grow your business in the coming years. You’ll do well to find a security partner that can grow with you.
In Conclusion
The cybersecurity landscape has changed, and finding a solution that fits your needs can be challenging, given the ever-shifting list of suppliers out there. Fortunately, it’s far from impossible, and your team just needs to abide by a few simple tips to get the job done.
By mapping your current state and identifying gaps, avoiding one-dimensional solutions (which require you to become a guinea pig), reading third-party reviews, and considering the long-term scalability of the solution you choose, you can secure the right technology for your team, and be confident you've done your homework before presenting the solution to your superior. This process also allows you to compare and contrast solutions, identifying opportunities to replace your existing solutions with something more effective, for example.
While selecting a cybersecurity vendor can feel difficult, it’s a critical responsibility, and doing it well helps ensure the health of you company both now and in the future.
The CyberXchange Solution
Struggling to find the ideal vendor or consultant to help close a critical gap in your cybersecurity program? Try CyberXchange today to quickly and easily find products and services mapped to your specific compliance gaps.
.svg)