The Complete Guide to Achieving CIS Compliance
CIS helps organizations follow 18 prioritized actions to ensure a robust security posture. It's so effective that the top five controls are designed to prevent almost 90% of the most common attacks.
Dive into this comprehensive CIS guide to discover who should be CIS compliant, how it applies to your organization’s risk profile, CIS best practices, and the benefits of aligning with this framework.

What is the CIS Framework?
CIS is a cybersecurity framework created by the Center for Internet Security, which offers best practice recommendations to protect organizations from cyber threats.
To combat these threats, CIS developed a clear-cut, hands-on framework that focuses on the top 18 most critical controls needed for security. You can adopt these controls to establish a core cybersecurity program and then expand with additional controls and sub-controls over time.
The CIS framework is developed and supported by various IT experts from different sectors, including private companies and governments, whose goal is to improve cybersecurity through non-profit efforts.
Who Needs to Comply with CIS?
Although it’s not required by law, every company, regardless of its size, should comply with CIS to achieve a better security posture.
Why? Because adopting CIS controls helps you build a strong defense against cyber-attacks, provides tools to respond to breaches, stops attacks from spreading within your network, and limits damage to other systems.
To become CIS compliant, you don't need a formal certification or assessment; you can self-evaluate through planning and mitigation. The key is to document and measure the effectiveness of your CIS controls. We recommend creating and recording supporting policies, procedures, and critical metrics, including specifications and configuration requirements.
The 5 Driving Principles of CIS Controls
As cyber attacks increase globally, cybersecurity professionals have been overwhelmed with advice on protecting their systems. That’s why the CIS framework is built upon five fundamental principles that are easy to follow for everyone:
1) Offense Informs Defense
CIS Controls are constantly being updated to defend against the newest and most latent threats. This framework is data-driven, since it prioritizes actions based on attacker behavior and how to stop it.
2) Focus
This framework helps prioritize the most critical things that a defender needs to implement to prevent the most critical risks.
3) Feasible
All individual recommendations (safeguards) must be specific and practical to implement
4) Measurable
Every control must be measurable. CIS recommends to simplify or remove ambiguous language to avoid misinterpretation.
5) Align
All controls are designed to map over to other governance and regulatory frameworks.

What Are the 18 CIS Critical Security Controls?
Unlike more extensive frameworks, CIS Critical Security Controls, or CIS CSC, provides a list of 18 high-priority controls for organizations at any maturity level. It also includes 150+ specific sub-controls for building or enhancing cybersecurity practices.
The best part? Once you abide by CIS compliance standards, you will likely comply with many other standard security frameworks. These controls and sub-controls directly map to other cybersecurity and data privacy frameworks like NIST 800-53, HIPAA, the ISO/IEC 27000 family, and more.
We’ve summarized each control to make them easy to read and understand.
Here’s a quick overview of each one:

Overview: Actively manage (inventory, track, and correct) all enterprise assets to accurately know which ones need to be monitored and protected. This will also support identifying unauthorized and unmanaged assets to remove or remediate.
Why is this control critical? Enterprises cannot defend what they can’t see. Managed control of all enterprise assets plays a critical role in security monitoring, incident response, system backup, and recovery.

Overview: Actively manage all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution.
Why is this control critical? A complete software inventory helps prevent attacks, as attackers continuously scan target enterprises looking for vulnerable software. Management of software assets is also important to identify unnecessary security risks.

Overview: Develop processes and technical controls to identify, classify, securely handle, retain, and dispose of data.
Why is this control critical? Protecting data is critical to prevent unauthorized access and breaches that could lead to financial loss, reputational damage, and regulatory penalties.

Overview: Establish and maintain the secure configuration of enterprise assets and software.
Why is this control critical? Default configurations for enterprise assets and software from manufacturers and resellers are typically geared towards being easy to use and deploy. If not properly managed and configured, they could expose your organization to security gaps and vulnerabilities.

Overview: Use processes and tools to assign and manage authorization to credentials for user accounts, including administrator accounts, as well as service accounts, to enterprise assets and software.
Why is this control critical? Threat actors find it easier to gain unauthorized access to your enterprise assets or data using “valid credentials” rather than brute-forcing or hacking the systems. Proper access control can easily stop this.

Overview: Use processes and tools to create, assign, manage, and revoke access credentials and privileges for user, administrator, and service accounts for enterprise assets and software.
Why is this control critical? Accounts should only have the minimal authorization needed for the role. This guarantees that fewer accounts are exposed to overly permissive privileges, reducing the number of potential targets while avoiding security issues later down the road.

Overview: Develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate and minimize the window of opportunity for attackers.
Why is this control critical? Continuous vulnerability management helps identify and fix weaknesses before they can be exploited by attackers.

Overview: Collect, alert, review, and retain audit logs of events that could help detect, understand, or recover from an attack.
Why is this control critical? Proper log management provides valuable insights into suspicious activities and helps in forensic investigations.

Overview: Implement security measures for email and web browsers to protect against phishing, malware, and other web-based threats.
Why is this control critical? Email and web browsers are common entry points for attacks; securing them reduces the risk of these threats.

Overview: Deploy and manage anti-malware tools to protect enterprise assets from malicious software.
Why is this control critical? Regular updates and scans help detect and remove malware, preventing potential damage and data breaches.

Overview: Set and maintain data recovery standards to allow restoration of enterprise assets to their original trusted state before any security incidents took place.
Why is this control critical? Robust data recovery capabilities minimize downtime and data loss during a disaster.

Overview: Secure and manage network infrastructure, ensuring proper segmentation, monitoring, and configuration to prevent unauthorized access and vulnerabilities.
Why is this control critical? Proper network management ensures reliable and secure communication within the enterprise. Furthermore, network security is a constantly changing environment that needs continuous oversight to avoid security degradation over time.

Overview: Continuously monitor network traffic and implement defense mechanisms to detect and respond to potential threats in real-time.
Why is this control critical? Continuous monitoring helps in maintaining the security and integrity of network traffic.

Overview: Provide regular security awareness training and skills development for all personnel to foster a security-first culture.
Why is this control critical? Educated personnel are less likely to fall victim to social engineering attacks, more likely to detect and report incidents, and more likely to follow security best practices.

Overview: Manage and monitor third-party service providers to ensure they meet the enterprise's security requirements and mitigate risks associated with outsourcing.
Why is this control critical? Ensuring service providers adhere to security requirements reduces the risk of breaches originating from third parties.

Overview: Manage the security life cycle of in-house developed, hosted, or acquired software to prevent, detect, and remediate security weaknesses before they can impact the enterprise.
Why is this control critical? Regular code reviews and vulnerability assessments help maintain the security of applications, preventing exploitation of software vulnerabilities.

Overview: Develop and maintain an incident response plan to quickly and effectively address security attacks.
Why is this control critical? A well-prepared response plan minimizes the impact of incidents and speeds up recovery.

Overview: Last but not least, regularly conduct testing procedures and attack simulations to identify and address security weaknesses.
Why is this control critical? Penetration testing helps improve the overall security posture by simulating real-world attacks and finding vulnerabilities before attackers do.
Steps to Comply with CIS Controls
If you’re ready to implement CIS Controls, it’s important to first understand how controls are prioritized. You should start at control 1 and work your way through the rest. To help facilitate this scalability, the 18 controls are broken into three implementation groups.
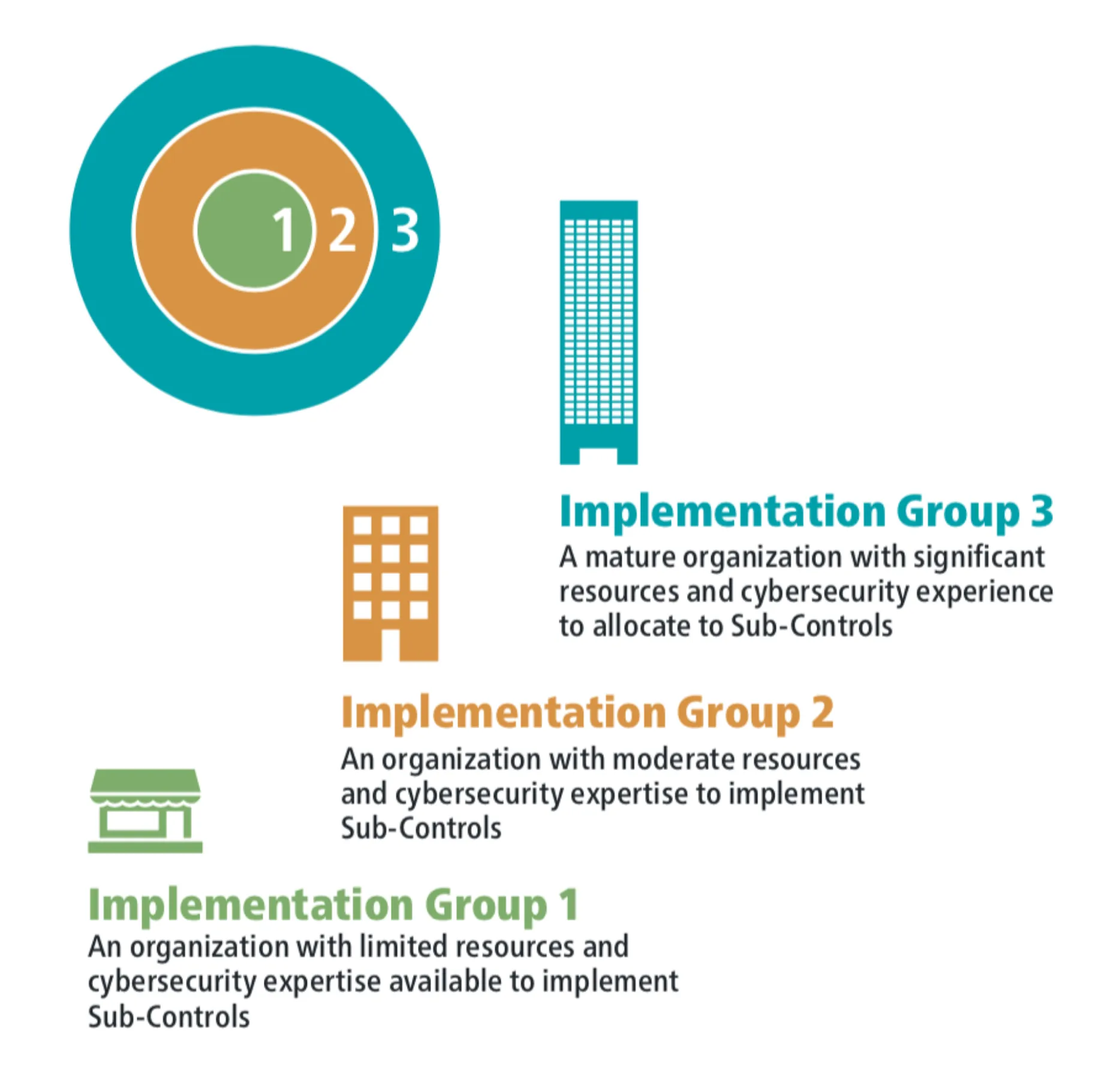
What are CIS Implementation Groups?
CIS Implementation Groups (IGs) are a categorization framework designed to help organizations prioritize the implementation of CIS Controls based on their specific needs and resources. Out of a total of CIS top 18 controls and 153 safeguards (sub-controls) — the number of safeguards an enterprise is expected to implement increases based on its size, resources, and cybersecurity maturity.
CIS Implementation Group 1 (IG1)
IG1 defines essential cyber hygiene and represents a minimum standard of information security for all enterprises.
An IG1 enterprise is small to medium-sized with limited IT and cybersecurity expertise dedicated to protecting IT assets and personnel. IG1 assists enterprises with limited cybersecurity expertise in thwarting general, non-targeted attacks.
Number of safeguards: 56 out of 153
CIS Implementation Group 2 (IG2)
IG2 assists enterprises in managing the IT infrastructure of multiple departments with differing risk profiles. It aims to help enterprises cope with increased operational complexity.
An IG2 company typically handles sensitive client or enterprise information and can tolerate brief service interruptions.
Number of safeguards: 74 out of 153
CIS Implementation Group 3 (IG3)
IG3 assists enterprises (typically large-scale ones) with IT security experts to secure sensitive and confidential data. It aims to prevent and/or lessen the impact of targeted attacks from sophisticated adversaries and reduce the impact of zero-day attacks.
Number of safeguards: 23 out of 153
Understanding CIS Benchmarks and CIS Hardened Images
In addition to CIS Controls, the cybersecurity community helped create CIS Benchmarks that outline more than 100 configuration guidelines for more than 25 vendor product families to reduce the risk of cyber threats. These can be used in systems like Windows, Linux, Oracle MySQL, MongoDB, AWS, and more.
CIS Benchmark compliance exists for various different:
- Operating systems
- Server software
- Cloud providers
- Mobile devices
- Network devices
- Desktop software
- Multi-function print devices
Moreover, CIS benchmarks are routinely updated, each consisting of multiple configuration profiles, which are categorized as follows:
Level 1: Base recommendations you can quickly implement that should not impact performance or hinder operations.
Level 2: These are “defense-in-depth” recommendations that, if not implemented properly, may adversely affect your operations.
Level 3 (STIG compliance): CIS Benchmarks specify a Level 3 STIG profile that is designed to help organizations comply with the Security Technical Implementation Guide (STIG), written to meet US government defense requirements. When you configure your systems according to the CIS STIG Benchmarks, your IT environment will be both CIS and STIG compliant.
CIS Hardened Images
In addition to CIS Benchmarks, CIS also has pre-configured virtual machine images that integrate CIS Benchmark standards. Unlike a standard virtual machine, a hardened virtual machine is configured to limit weaknesses threat actors could exploit. You can use hardened virtual machines as secure computing environments with protection against a variety of threats, including unauthorized access, data exfiltration, denial of service, and other risks.
CIS hardened images are available across a variety of platforms, including:
- Amazon Web Services (AWS Marketplace, AWS IC, and AWS GovCloud)
- Microsoft Azure (Azure Marketplace and Azure Gov Marketplace)
- Google Cloud Platform
- Oracle Cloud Marketplace
Want to accelerate your CIS compliance process?
With Apptega’s cybersecurity and compliance software, you can use streamlined questionnaires, integrations to your sources of truth, and framework crosswalking to fast-track CIS compliance and quickly realize its benefits.
How to Choose the Right CIS Compliance Tool
Although CIS compliance audits are not required to comply with the framework, your security team can use CIS controls and benchmarks as a great internal auditing tool. The question then becomes: which tool should I choose to automate this process?
CIS provides an Excel spreadsheet to track and manage compliance with CIS. But why make this process so tedious and complicated? Apptega is the best platform to achieve and maintain CIS compliance — being purpose-built for organizations and security providers of all sizes.
Why choose Apptega to comply with CIS?
The Apptega platform makes it dead simple to build, manage, and report your cybersecurity and compliance programs. It puts an end to complex and time-consuming spreadsheets.
Apptega allows you to manage all your compliance programs (including CIS) as a single security tool with framework crosswalking, integrations, and AI-based remediation to boost your efficiency.
Key benefits for MSPs and MSSPs
✔️ Go to market with a fully-formed CIS compliance solution that enables you to easily layer on your cybersecurity services to meet controls.
✔️ Easily map CIS controls to 30+ other frameworks like CMMC, ISO 27001, NIST, PCI DSS, and more.
✔️ Grow annual recurring revenue by offering continuous, market-differentiated compliance services that make your clients stickier.
✔️ Boost internal efficiency by using a single platform to manage all your customers’ programs end to end.
Key benefits for in-house teams
✔️ Cut the time it takes to become compliant with CIS and other industry-standard cybersecurity or privacy frameworks in half.
✔️ Build a robust CIS program that lowers your insurance burden and guards your business against that 'oh s***!' moment.
✔️ Evaluate your cybersecurity posture 2X faster with questionnaire-based CIS templates to quickly identify gaps and start remediation.
Key Takeaways Regarding CIS Compliance
When using CIS controls or any other security framework, remember that “it’s not about the list.” While many sources provide credible security recommendations, the CIS framework should be seen as a starting point for building your continuous compliance program.
It is important to look for the ecosystem that grows up around the list and ask the following questions:
- Where can I get training, complementary information, and explanations?
- How have others implemented and used these recommendations?
- How will I measure progress or maturity?
- How does this align with the myriad regulatory and compliance frameworks that apply to me?
With Apptega, organizations of all sizes, including hundreds of Fortune 500 enterprises and Managed Security Service Providers (MSSPs), are simplifying cybersecurity and compliance management. Our platform is at the intersection of simple user experiences and state-of-the-art technology, providing an innovative platform paired with industry frameworks to build, manage, and report great cybersecurity and compliance.
To learn more about how Apptega can help you become CIS compliant, start your free trial here.
CIS FAQs
The Center for Internet Security oversees CIS controls, benchmarks, and hardened images. However, a diverse group of IT and security professionals works together to maintain these best practices based on the current threat landscape and emerging technologies.
Although CIS doesn’t have a formal compliance requirement, abiding by CIS standards is a good idea. If you’re a small organization with limited resources, you may find the first six of 18 controls in Implementation Group 1 sufficient for your needs. However, as your organization scales over time (or if you’re already a medium or large-scale organization) you can benefit from adopting additional CIS controls and sub-controls for a more secure technology environment.
Unlike other more complex cybersecurity frameworks, organizations of all sizes can tackle CIS implementation. First, review CIS controls and sub-controls. Next, evaluate your organization’s resources and experience. If you discover you have limited resources and security expertise, begin your program with the controls in Implementation Group 1. If you have moderate resources and expertise, implement Group 1, then move on to Group 2. Finally, as your program and organization mature, move to Implementation Group 3.
There are a number of benefits your organization could reap from adopting CIS controls. First, these controls, which are globally recognized as industry best practices, can help you reduce cybersecurity framework and tools overload so you can focus on adopting and implementing critical security practices to secure your organization now and then build onto your program over time. Adopting CIS controls can help give you the insight you need to detect vulnerabilities and other security issues, identify which ones may have the most critical impact on your organization, build defenses to protect your most critical applications and services, and then respond to threats as they occur to quell damage and prevent future attacks.
CIS Benchmarks are best-practice security configuration guidelines to secure target systems such as operating systems, server software, cloud providers, mobile devices, network devices, desktop software, and multi-functional print devices.
Yes, they are free.
The CIS controls were established in 2008 by an international, grassroots consortium that includes companies, government agencies, institutions, and individuals from all areas of the cybersecurity ecosystem. The volunteers of this framework had one goal in mind: to prioritize effective, hands-on defense against latent security threats.
Because CIS controls are updated regularly to keep your security resilience up-to-date.
No, these controls should be a complement and not a replacement. Still, it is worth noting that CIS controls map to most major compliance frameworks like NIST 800 52, ISO 27001, and more.
Think of CIS controls as a more general set of guidelines to defend against the most prevalent and imminent cyberattacks, whereas the CIS benchmarks are just practical steps for securing operating systems, middleware, applications, and network devices. The security configurations from the benchmarks are still referenced in CIS control 4 as a recommendation to secure hardware and software on laptops, workstations, servers, and mobile devices.
They are very similar. However, NIST is more focused on reducing cyber risk while CIS focuses on cyber hygiene and protection against common threats. For example, strict standards that may require certification and audits like CMMC are based on NIST guidelines, whereas CIS is more of an actionable, hands-on framework to defend against threats. Check out this blog to learn more.
Some companies and public organizations include: Boeing, Softbank, Tenable, Citizens Property Insurance, the US states of Arizona and Colorado, and many more.
The SANS institute is a great reference since they provide training that you can access here. In addition, Apptega has great resources such as blogs, whitepapers, and webinars about CIS that can help you navigate your journey toward adopting CIS Controls as part of your security arsenal.
Still have a question?
Get in touch with us and we would be happy to help.
Ready to get started?
Request a no-risk 14-day free trial to see how you can create a sticky compliance-as-a-service offering with Apptega.
.svg)






