Introduction
Key Takeaways

This is a guest post by Frank Kyazze, Founder & CEO, GRC Knight.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) has long been a beacon for entities seeking to navigate the complexities of cyber risk management. With the anticipated release of NIST CSF 2.0 in early 2024, a new chapter in cybersecurity governance is set to unfold, offering enhanced guidance and an expanded scope to accommodate the needs of a broader audience.
The Genesis and Evolution of NIST CSF
Originating from a 2013 Executive Order, the NIST CSF was crafted in collaboration with the private sector, aiming to provide a voluntary framework grounded in established standards and best practices. Its core components — the Core, Tiers, and Profiles — have served as the foundation for understanding, evaluating, and communicating cybersecurity risks, tailored to the unique demands and capacities of individual organizations:
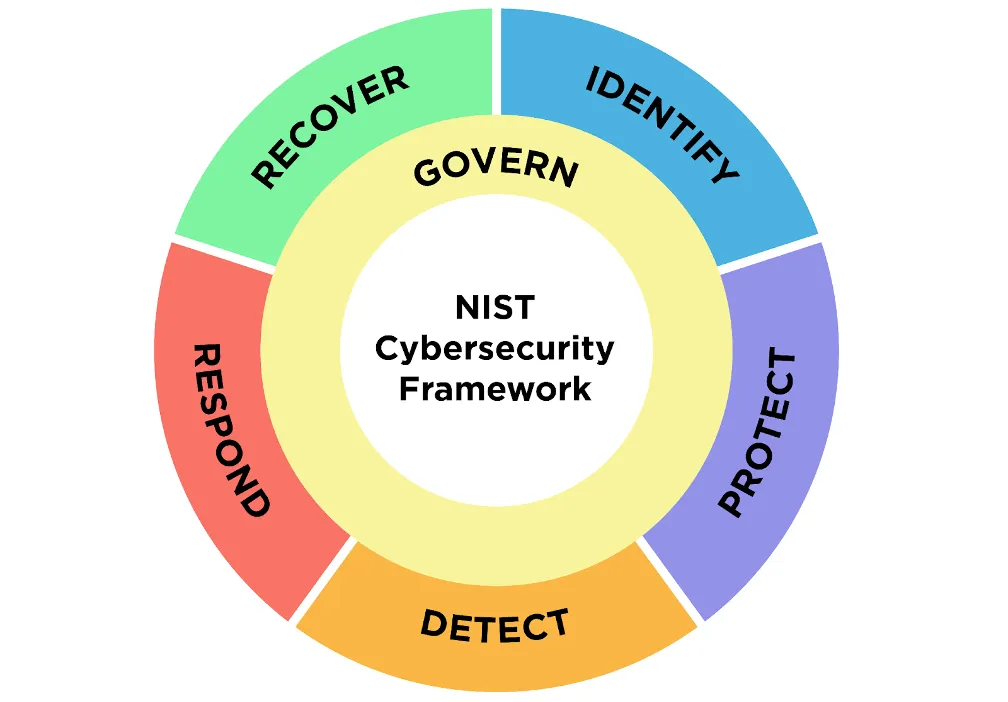
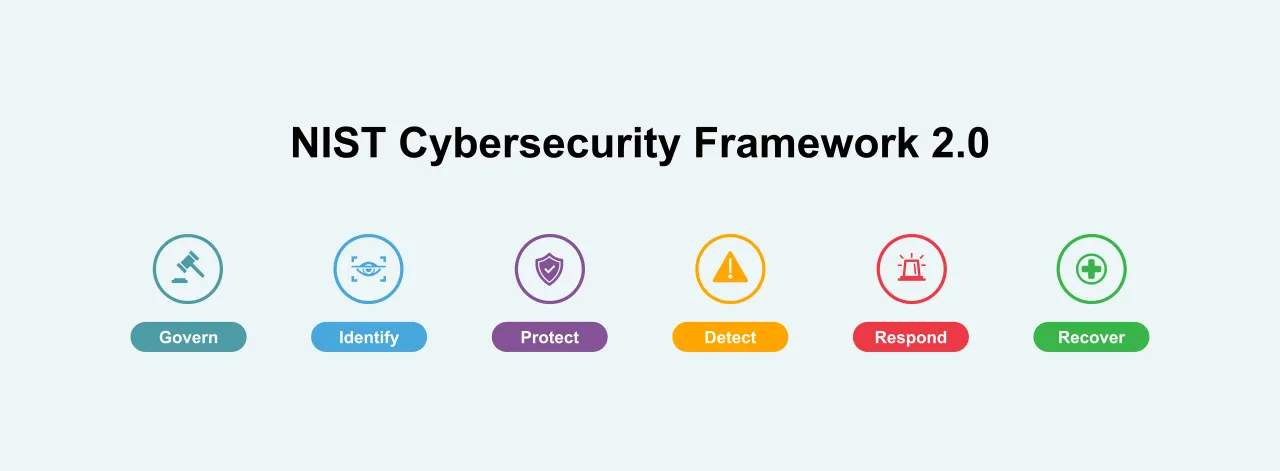
- Core - The Core of the NIST CSF provides a set of cybersecurity activities, desired outcomes, and informative references that are common across critical infrastructure sectors. It is organized into six primary functions: Govern, Identify, Protect, Detect, Respond, and Recover. These functions offer a high-level, strategic view of an organization's management of cybersecurity risk by enabling a comprehensive approach to cybersecurity.
- Tiers - The Tiers in the NIST CSF describe an organization's view of cybersecurity risk and the processes in place to manage that risk. Tiers range from Partial (Tier 1) to Adaptive (Tier 4), reflecting a progression from informal, reactive responses to approaches that are agile, risk-informed, and anticipatory.
- Profiles - Profiles represent the outcomes based on business needs that an organization has selected from the Framework Categories and Subcategories. Profiles are used to identify opportunities for improving cybersecurity posture by comparing a "Current" Profile (the "as is" state) with a "Target" Profile (the "to be" state).
Key Enhancements in NIST CSF 2.0
The journey from NIST CSF to its 2.0 iteration marks a significant evolution, reflecting broader usage and inclusivity across different organization sizes, sectors, and maturity levels. Here’s a closer look at the pivotal changes and new introductions in version 2.0:
- Expanded Scope: The revision aims to be universally applicable, with explicit guidance designed to empower even smaller businesses to leverage the framework effectively.
- Introduction of the "Govern" Function: A landmark addition, the Govern function emphasizes the integration of cybersecurity with overarching enterprise risk management, highlighting the vital role of governance in achieving cybersecurity objectives.
- Restructured Core Functions: The original functions (Identify, Protect, Detect, Respond, and Recover) have been meticulously revised, with a clear delineation of key goals and the migration of governance-related components to the newly established Govern function.
- Enriched Guidance Around Profiles: Version 2.0 unfolds extensive revisions and expansions in profile guidance, featuring detailed examples, step-by-step creation and usage instructions, and an enriched template in Appendix A to facilitate targeted action planning.
The Strategic Imperative of the Govern Function
The Govern function of NIST CSF 2.0 ushers in a new era where cybersecurity is intricately woven into the organizational tapestry, emphasizing its importance at the boardroom table. This strategic integration extends beyond IT departments, underscoring the reality that cybersecurity risks are now critical business risks.
When NIST's guidance is synchronized with other regulatory frameworks — be it HIPAA for healthcare or GDPR for privacy — it cultivates a robust governance culture that aligns cybersecurity with enterprise-wide risk management and compliance obligations. This alignment is not just about avoiding penalties. It's also about ensuring that cybersecurity considerations are inherent in all aspects of business operations, from mergers to everyday decision-making.
Elevating cybersecurity to a governance issue transforms how senior management and boards of directors approach digital threats. It's a shift from reactive measures to proactive oversight, instilling a risk-aware and ethical mindset across corporate echelons.
By integrating the Govern function into their cybersecurity strategies, organizations empower themselves to make more informed strategic decisions, balancing cybersecurity risks against operational and financial considerations. It's a holistic approach that ties together strategic planning, risk management, and business continuity, ensuring that cybersecurity is embedded in the very DNA of the organization's decision-making processes.
The benefits of this integration are manifold, from enhanced regulatory compliance to fortified stakeholder confidence. Customers, partners, and investors take notice when an organization demonstrates a mature, framework-aligned approach to cybersecurity governance. It's more than just a compliance checklist — it's a comprehensive strategy that communicates reliability, resilience, and a forward-thinking attitude in a digital landscape fraught with uncertainties.
Ultimately, the Govern function is not just a component of NIST CSF — it's a lighthouse guiding organizations to a secure and resilient future in the digital economy.
A Closer Look at Core Function Changes
The introduction of the Govern function in CSF 2.0 marks a significant shift in how we approach cybersecurity. Rather than treating it as a series of discrete tasks to check off a list, it’s now recognized as a dynamic element of organizational strategy. This change not only resonates with the framework's adaptable nature but also reinforces the need for a holistic view of cyber risks.
Integrating Govern with Core Functions
Consider a company that has traditionally focused on the original NIST CSF core functions: Identify, Protect, Detect, Respond, and Recover. While these functions have served it well in creating a robust cybersecurity posture, the addition of the Govern function enables the company to elevate its strategy.
Integration of the Govern function means that cybersecurity considerations are now embedded in the corporate governance framework. This enables the board and senior management to take active roles in directing cybersecurity initiatives, ensuring these efforts are fully aligned with business objectives and risk management strategies.
Practical Example: A Coherent Cybersecurity Strategy
A practical example of this integration might involve rollout of a new mobile application. With the Govern function in place, the development of this application begins with high-level strategic discussions, considering not only the technical aspects but also alignment with overall risk tolerance and regulatory compliance needs:
- Identify: Identify the digital assets most critical to the new application, such as customer data and proprietary algorithms, to understand where and how this data flows.
- Protect: Design security features into the application from the outset, implementing strong encryption and multi-factor authentication as part of the protection strategy.
- Detect: Implement monitoring systems to detect potential security breaches in real-time, integrating with the existing cybersecurity infrastructure.
- Respond: Develop response plans in anticipation of various breach scenarios, ensuring swift and effective action to mitigate any damage.
- Recover: Establish recovery processes to quickly restore any lost data and services, minimizing customer downtime.
The Benefit of a Coherent and Strategic Approach
Incorporating the Govern function into this process ensures each of these steps is not only technically sound but also strategically aligned with broader objectives. This coherence means that cybersecurity is not a siloed IT issue but a cross-departmental responsibility that encompasses legal, regulatory, and reputational considerations.
Moreover, the Govern function mandates regular reviews and updates to these strategies, ensuring adaptation to the evolving cyber threat landscape. It also promotes transparency and accountability, with the board receiving regular updates on cybersecurity efforts, allowing for informed decision-making and resource allocation.
Community Profiles: A Collaborative Edge
NIST CSF 2.0 introduces the concept of "Community Profiles," which leverages the collective intelligence of various organizations. It's a collaborative effort where groups — be they financial institutions, healthcare entities, or educational institutions — use the common language of the CSF to create shared cybersecurity risk management blueprints. These profiles are not just theoretical constructs. They are living documents, cultivated from real-world applications and shared challenges within these communities.
The NIST National Cybersecurity Center of Excellence (NCCoE) plays a pivotal role here, facilitating the development of Community Profiles that address specific use cases. These profiles are then made available in the NCCoE’s Framework Profile Resource Center, serving as a repository of knowledge and a starting point for organizations seeking to refine their own cybersecurity postures.
Customized Profiles: Beyond the Baseline
The expanded profile guidance in NIST CSF 2.0 is akin to a masterclass in cybersecurity customization. It empowers organizations to go beyond baseline protections and tailor their cybersecurity measures to their unique risk landscapes and business objectives.
With access to templates and detailed instructions, organizations can more effectively interpret the framework’s practices in a manner that aligns with their specific operational contexts. This is particularly beneficial for small and medium-sized businesses that may not have the resources to develop such frameworks from scratch. They can adapt the insights from Community Profiles, modifying them as necessary to address their unique risks and cybersecurity goals.
Facilitating Personalized and Effective Risk Management
The result of leveraging the expanded profile guidance is a more nuanced and effective risk management strategy. Organizations can articulate their current cybersecurity postures, envision desired states, and chart transition paths. The guidance also includes benchmarks and metrics, helping organizations measure progress and make informed decisions about where to invest in cybersecurity.
The Practical Benefits of Expanded Profile Guidance
Consider a regional hospital looking to enhance its cybersecurity defenses against ransomware attacks. By using the NIST CSF 2.0's expanded profile guidance, the hospital can develop a profile that not only incorporates general best practices but also addresses the specific threats and regulatory requirements it faces.
The hospital can leverage a Community Profile developed for the healthcare sector as a starting point, customizing it to a particular electronic health record system, patient portal, and other unique technologies and workflows. This enables a focused approach to fortifying defenses where they matter most.
Navigating the Future with NIST CSF 2.0
As organizations stand on the cusp of embracing NIST CSF 2.0, the enhancements and expansions introduced in this version promise a more inclusive, adaptable, and strategic framework for cybersecurity risk management. By integrating governance into the core of cybersecurity practices and offering refined guidance for tailoring the framework to individual needs, NIST CSF 2.0 is poised to be a critical tool in the arsenal of organizations aiming to fortify their cyber defenses in an increasingly digital world.
As we venture into this new era of cybersecurity governance, the anticipation for NIST CSF 2.0 underscores the collective commitment of the cybersecurity community to elevate standards, enhance resilience, and foster a culture of proactive cyber risk management. With its expanded scope, strategic enhancements, and comprehensive guidance, NIST CSF 2.0 is set to redefine the benchmarks for cybersecurity excellence across industries.
.svg)
