NIST 800-53: A Comprehensive Guide
Whether embarking on a new journey towards NIST 800-53 compliance or enhancing existing security measures, this guide will help you streamline the process and continue to uphold your commitment to national security.

In today’s interconnected world, safeguarding information systems and data is not just a necessity but a cornerstone of trust, particularly for entities engaged with the U.S. Federal Government.
The NIST Special Publication 800-53, developed by the National Institute of Standards and Technology (NIST), serves as a comprehensive guide for securing federal information systems and organizations. Dubbed the "Control Catalog," this framework outlines extensive security controls and privacy guidelines to protect against a myriad of threats, including cyber attacks, natural disasters, and human errors.
Why is adherence to NIST 800-53 pivotal? For organizations, particularly those offering cloud-hosted services to federal agencies with classified data, compliance with NIST 800-53 is synonymous with establishing a robust security posture. It's a foundational framework not only for meeting federal standards like FedRAMP but also adaptable to various other compliance requirements like HIPAA and PCI DSS.
This guide demystifies NIST 800-53, providing a structured approach to navigate its complexities:
- NIST 800-53 Revisions: Insights into the evolution of the framework, including key updates in recent revisions.
- NIST 800-53 Control Families Explained: Detailed examination of the 20 control families and their respective roles in securing information systems.
- Navigating NIST Compliance Software: Guidance on leveraging software solutions for effective compliance management.
- Certification and Compliance Checklist: Step-by-step walkthrough of the compliance process, aligned with the Risk Management Framework.

What is NIST 800-53?
NIST 800-53 is a cybersecurity framework established by the National Institute of Standards and Technology (NIST), which is integral for protecting sensitive government information and systems against a diverse array of threats, including cyber attacks, natural disasters, privacy risks, and human errors. It provides comprehensive guidelines for selecting and specifying security controls within organizations, particularly those dealing with federal information systems.
NIST 800-53 is closely tied to NIST 800-37, the Risk Management Framework (RMF), and serves as a detailed catalog of specific security controls. These controls are crucial for organizations to evaluate and assess their implementation of security measures to comply with federal standards.
NIST first published these standards in 2005 to facilitate compliance to the Federal Information Security Management (FISMA) Act of 2004, which requires agencies to develop and maintain minimum standards to protect federal information and federal information systems. The NIST 800-53 controls make up a cybersecurity risk management framework that can meet the FISMA requirements.
Who needs to be compliant with NIST 800-53?
NIST 800-53 compliance is primarily mandated for U.S. federal agencies, except those related to national security. First published in 2005, all federal agencies were required to be compliant within one year.
However, the NIST 800-53 risk management framework can also be used by other organizations of all sizes and across diverse industries. The framework is closely related to NIST 800-171, which is required for organizations that work with the federal government and access controlled unclassified information (CUI).
More specifically, this framework is crucial for:
- Cloud Service Providers (CSPs): Those authorized under FedRAMP are required to adhere to NIST 800-53 controls.
- Federal Contractors: Organizations contracted with federal agencies must comply, as NIST 800-53 informs the security standards these contractors should meet.
- Entities under FISMA: Since NIST 800-53 forms the basis for the Federal Information Security Management Act (FISMA), state agencies and contractors partnering with the federal government are also implicated.
Overall, any organization involved in business with the U.S. government, directly or indirectly, should consider compliance with NIST 800-53 as part of their cybersecurity strategy.
NIST 800-53 Revisions in a Nutshell
Each revision of NIST 800-53 had the goal to enhance and update the framework to respond to evolving cybersecurity needs and technological advancements.
Here’s what the two most recent revisions included:
- Revision 4 (April 2013): This update was driven by significant changes in the threat landscape. It introduced controls focused on privacy and addressed supply chain security, though not as a distinct family of controls. This revision marked a shift towards integrating privacy considerations into the broader security framework.
- Revision 5 (September 2020): The latest revision represents a more significant overhaul. Key changes include relocating the catalog of controls to a separate document (NIST SP 800-53B) and introducing a new family of controls dedicated to supply chain risk management. This revision also put more emphasis on privacy, integrating privacy controls with security controls and aligning them better with broader cybersecurity and risk management strategies.
NIST SP 800-53 v5 consists of 20 control families and more than 1,000 related controls. Interestingly, this revision includes the removal of the word “federal” to clarify these standards are not just for federal agencies, but may be applicable to other organizations and to encourage more widespread use of this framework.
Here’s a breakdown of the main changes in this fifth revision:
- Adjustments to both technical content and structure
- Controls are now outcome-based
- Consolidation of the control catalog for systems and organizations
- Supply chain risk management now included and integrated in other control families
- Control selection process now separate from controls
- Control baselines and other guidance moved to NIST SP 800-53B “Control Baselines for Information Systems and Organizations”
- Clarifications between requirement and control relationships and security and privacy controls
- New practice controls that address current threats
All these revisions reflect NIST's commitment to keeping the framework both comprehensive and adaptable, ensuring it remains a vital tool for organizations in managing their cybersecurity risks in an ever-changing digital environment.
Want to accelerate your NIST 800-53 compliance process?
With Apptega’s cybersecurity and compliance software, you can use streamlined questionnaires, integrations to your sources of truth, and framework crosswalking to run through NIST 800-53 assessments and audits like a breeze.
Why NIST 800-53 Compliance Matters
There are many benefits to becoming NIST 800-53 compliant even when you’re not required to do so. These standards can benefit any organization that processes, transmits, or stores sensitive or protected data, which is essentially any company out there.
Here are some of the benefits of NIST 800-53 compliance:
Enhanced Security Posture: Implementing NIST 800-53's controls significantly bolsters an organization's defense against a wide range of cyber threats across different systems, including modern assets like IoT and IIoT.
Federal Market Access: Compliance is often a prerequisite for doing business with federal agencies, opening doors to new market opportunities.
Risk Management: The framework facilitates a comprehensive approach to risk assessment and management, crucial for maintaining robust security. You can also use it to establish your baseline security standards and then mature your processes over time.
Trust and Credibility: Adherence to this widely recognized standard demonstrates an organization's commitment to security, building trust with partners and customers.
Alignment with Other Standards: NIST 800-53's comprehensive nature makes it a solid foundation for complying with other standards such as PCI DSS, CMMC, NIST 800-171, and more, streamlining overall compliance efforts. Additionally, if you use compliance software that includes framework crosswalking, complying with frameworks that have shared controls becomes a walk in the park.
Cohesive Security Approach: Unify your security protocols under specific security groupings to identify, protect, detect, respond, and recover from cyber risks.
NIST 800-53 Control Families
NIST 800-53 encompasses more than 1,000 base controls and control enhancements spread across 20 control families. Each family represents controls specific to a particular aspect of security and privacy.
Here is an overview of these control families and their significance:

These controls limit access to information systems, ensuring that access is granted only to authorized individuals based on the principle of least privilege.

This family focuses on ensuring that all personnel are adequately trained and aware of the security risks, as well as their responsibilities in mitigating these risks.

Controls in this family involve recording and examining activities in information systems to detect and respond to security incidents.

This family deals with the authorization of information systems and the ongoing assessment and monitoring of security controls.

These controls are dedicated to maintaining the integrity of systems and products through managing configurations.

Contingency planning controls are about preparing for, responding to, and recovering from system interruptions or disasters.

Ensures that the identity of users or systems is verified before granting access.

Establishes the capabilities for responding to and managing information system incidents.

Involves routine and emergency maintenance of information systems, considering the security impacts.

Focuses on protecting information in various formats from unauthorized access or alterations.

This family includes measures to safeguard physical resources and facilities of an information system.

Involves system security plans and guides the implementation and operation of information systems.

Provides a strategic view of the organization's information security program and is not applicable to individual systems.

Ensures the reliability and training of personnel with access to information systems

This control family addresses the processing and transparency of personally identifiable information.

Involves identifying and assessing risks to organizational operations, assets, or individuals.

Addresses the life cycle of information systems, including development, integration, and outsourcing decisions.

Protects the integrity of transmissions and information flows in information systems.

Focuses on protecting information and information systems against unauthorized changes.

A new addition that deals with reducing risks in the system's supply chain.
These control families provide a comprehensive approach to securing information systems, addressing a range of security and privacy concerns. It's important to note that while the controls are often listed in alphabetical order, organizations should prioritize their implementation based on specific needs, goals, and risk assessments.
Federal agencies are required to implement all controls, but other organizations may choose controls based on their specific environments and maturity levels.
NIST 800-53 Control Classifications
Apart from the control family groupings, all of the NIST 800-53 controls are differentiated by a classification, which is associated with their potential impact level.
These classifications align with FIPS 199 security objectives: confidentiality, integrity, and availability.
Here’s a quick look at each level and what they mean:
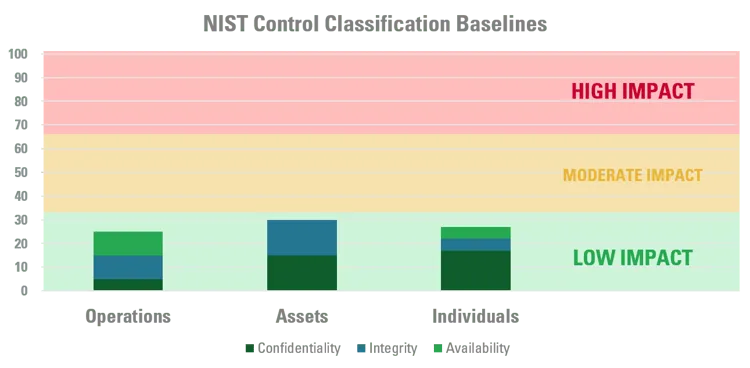
Low-impact baseline
The potential impacts related to all three of the security objectives (confidentiality, integrity and availability) are low. The potential impact is considered to be low if the loss of confidentiality, integrity, or availability is expected to have a limited adverse effect on operations, assets, or individuals.
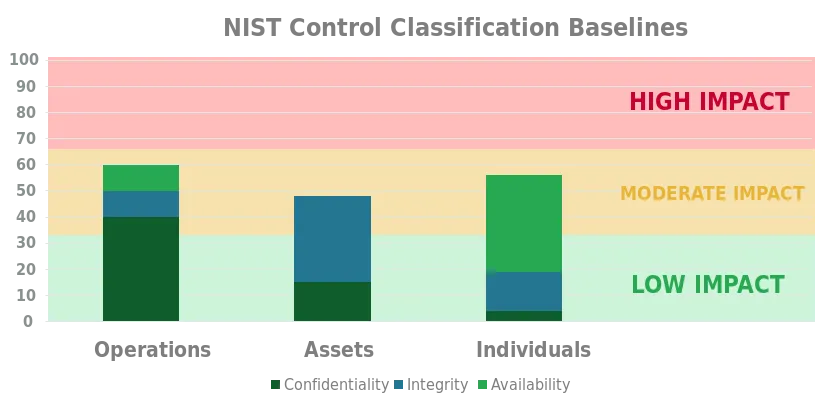
Moderate-impact baseline
The potential impact related to at least one of the three security objectives (confidentiality, integrity and availability) is moderate, and none of the potential impacts are greater than moderate. The potential impact is considered to be moderate if the loss of confidentiality, integrity, or availability is expected to have a serious adverse effect on operations, assets, or individuals.
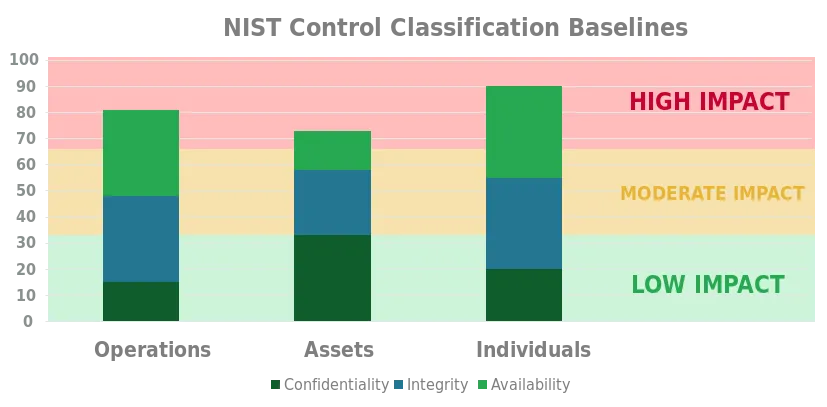
High-impact baseline
The potential impact related to at least one of the security objectives (confidentiality, integrity and availability) is high. The potential impact is considered to be high if the loss of confidentiality, integrity, or availability is expected to have a severe or catastrophic effect on operations, assets, or individuals.
A Guide to NIST 800-53 Control Implementation
The implementation of NIST 800-53's over 1,000 controls can be daunting, especially since they are not organized in a linear, progressive order.
For federal agencies, the challenge is even more significant as they are required to implement the entire suite of controls.
To make the task easier, NIST provides structured guidance to aid organizations in this process, presenting three distinct approaches for control implementation. Understanding these approaches is key to determining the most effective way to meet both security and privacy requirements:
1. Common Control Implementation
- Scope: These are controls that are universally applicable across an organization. They provide a foundational security level that benefits multiple information systems.
- Advantages: By implementing common controls, organizations can ensure a baseline security posture that is uniformly applied, reducing redundancy and simplifying compliance.
- Responsibility: Typically, the development and maintenance of these controls are centralized within the organization, often managed by a dedicated security or IT team.
- Examples: Security policies, physical and environmental protection measures, and organization-wide training programs.
2. System-Specific Implementation
- Scope: These controls are tailored to the unique requirements of individual information systems. They address specific security needs based on the system's function, data, and users.
- Advantages: System-specific controls allow for a more nuanced approach to security, addressing the unique risks and requirements of each system.
- Responsibility: The responsibility for these controls lies primarily with the system owners and their teams, who best understand the system's intricacies.
- Examples: Specific access controls for a financial system, encryption for a data storage system, or bespoke incident response procedures for a critical infrastructure system.
3. Hybrid Implementation
- Scope: Hybrid controls blend aspects of both common and system-specific controls. They are partially common across the organization but also require specific tailoring for individual systems.
- Advantages: This approach allows for a balance between broad applicability and system-specific relevance, ensuring a comprehensive security posture that adapts to varying needs.
- Responsibility: Hybrid controls involve collaboration between central security teams and individual system owners, leveraging insights from both perspectives.
- Examples: A centralized patch management system that requires specific configurations for different systems, or a network security protocol that adapts to the needs of various departments.
Integrating with System Development Lifecycle
Incorporating these approaches into your system development lifecycle can enhance their effectiveness. By aligning security control implementation with system design, development, and deployment phases, organizations can ensure that security and privacy are integral components of their information systems from the outset.
Each approach provides a different lens through which to view the control implementation, allowing organizations to strategize effectively based on their unique environment and requirements. It's crucial to assess the nature of your systems, the data handled, and the specific security needs to determine the most appropriate mix of these implementation approaches.
NIST 800-53 Compliance: A Complete Checklist
Unlike other cybersecurity frameworks, you don’t have to complete a formal certification process to be NIST 800-53 compliant; however, compliance with this framework is part of the FISMA Certification and Accreditation (C&A) process. If you’re a federal agency, you’re expected to be able to prove you’re NIST 800-53 compliant and that the controls you’ve adopted based on the framework's standards function as intended.
As with most compliance metrics, documentation is key, especially when conducting a self-assessment. Whether you’re running a self-assessment or are ready to conduct an internal audit to review NIST 800-53 compliance, here are a few steps you can take for success:
1. Assessment and Gap Analysis
Begin with a thorough assessment of your current security measures against the NIST 800-53 standards. Select the specific procedures related to each privacy and security control you want to assess. Don’t forget to include documentation such as existing policies and written procedures.
Identify gaps where your existing practices don't meet the required controls.
2. Prioritization and Planning
Prioritize the implementation of controls based on a your assessment. Focus first on controls that address the most critical vulnerabilities and threats to your organization.
3. Control Implementation
Implement controls using the common, system-specific, or hybrid approaches as appropriate for your organization.
Also, ensure that each control is properly documented, with clear procedures and guidelines for operation and maintenance.
4. Training and Awareness
Conduct training sessions for staff to understand the importance of NIST 800-53 controls and their role in maintaining compliance. This will help foster a culture of security within the organization where every employee is aware of and committed to the security protocols.
5. Continuous Monitoring and Improvement
Regularly monitor the effectiveness of implemented controls. Use audit management software to assess compliance continuously. Also, make sure you’re always up to date with changes in the threat landscape, technological advancements, and updates in NIST 800-53 revisions. Adapt and update your controls and strategies accordingly.
6. Documentation and Reporting
Maintain detailed records of all compliance activities, including risk assessments, control implementations, training records, and audit findings.
Also, make sure you prepare reports for internal stakeholders and regulatory bodies as required, demonstrating your compliance status and efforts.
NIST Compliance Software: Is There Such a Thing?
Achieving and maintaining NIST 800-53 compliance is a complex process that requires continuous monitoring, assessment, and adaptation. That’s why leveraging the right tool (no, Excel isn’t the right tool) can be a game-changer. It can not only simplify the process but also ensure thoroughness and accuracy. Here’s how specialized compliance software like Apptega can facilitate achieving and maintaining NIST 800-53 standards.
The Advantages of Using Cybersecurity and Compliance Software
Using compliance software can have a drastic impact on the speed and the cost of your NIST 800-53 compliance journey. Here are the main aspects a tool like Apptega can help with:
Simplified framework management: With questionnaire-based templates covering all the controls and subcontrols of the NIST 800-53, running your assessments and identifying gaps becomes dead simple.
Real-time reporting: Get instant access to the data and information you need to report on your cybersecurity posture and compliance at any time.
Framework crosswalking: By harmonizing controls across your frameworks through Apptega Harmony, you can quickly improve your program efficiencies by 50% or more.
Increased visibility: Demonstrate to your clients, key stakeholders, and the public that you are NIST 800-53 compliant with ease.
Collaborative environment: Facilitates collaboration among teams, making it easier to share information, assign tasks, and track progress.
Risk management: With Apptega’s Risk Manager tool, you can stack rank your risks and make sure you tackle the most pressing ones first.
For a detailed explanation of how you can use Apptega to consolidate the controls of NIST 800-53 and any other frameworks you need to comply with, watch this 4-minute demo video:
In short, software solutions like Apptega play a crucial role in simplifying and accelerating the NIST 800-53 compliance process. They provide a comprehensive, efficient, and user-friendly approach to managing the various facets of compliance, from initial assessment to ongoing monitoring and reporting.
NIST 800-53 FAQs
NIST 800-53 provides comprehensive security and privacy controls for federal information systems, aimed at protecting them against diverse threats like cyber attacks and natural disasters. Its primary purpose is to enhance the security posture and ensure compliance with federal cybersecurity standards.
NIST 800-53 comprises over 1,000 security and privacy controls, distributed across 20 control families.
The main difference between NIST 800-53 and NIST 800-171 is their target audience and scope: NIST 800-53 is designed for federal information systems and organizations, while NIST 800-171 targets non-federal entities handling Controlled Unclassified Information (CUI).
The main difference between NIST 800-53 and ISO 27001 is their scope and origin: NIST 800-53 is a U.S.-centric framework for federal information systems, while ISO 27001 is an international standard for information security management applicable to all organizations globally.
To implement NIST 800-53, first conduct a gap analysis to assess current security measures against the framework's standards, then prioritize and implement the relevant controls using a tailored approach for your organization. Regular monitoring, updating, and training are essential for maintaining compliance. Using a tool like Apptega can help streamline the entire process.
No. There is not a formal NIST 800-53 certification, however, becoming NIST 800-53 compliant is part of earning a FISM certification. Also, all federal agencies must be compliant to all NIST 800-53 standards and must be able to prove they have successfully implemented NIST 800-53 controls and that these controls function as intended.
The most current version of NIST 800-53 is Revision 5, which NIST released on Sept. 23, 2020. This version reflects an increase in control families—from 18 to 20—and even more controls, which now exceed more than 1,000. NIST adapted this version to be more in line with today’s threat landscape and adds new components, including new state-of-the-art practice controls and integrated supply chain risk management. To see the most recent version, visit https://csrc.nist.gov/News/2020/sp-800-53-revision-5-published.
FISMA is the Federal Information Security Management Act and part of the E-Government Act of 2002. FISMA outlines the importance of information security for federal agencies and establishes requirements for these agencies to protect federal information and federal information systems. NIST is responsible for establishing and updating standards and other compliance documents to meet FISMA requirements. One of those sets of standards is NIST 800-53, a risk management framework, that establishes base controls and control enhancements federal agencies are expected to adopt to meet FISMA mandates.
Still have a question?
Get in touch with us and we would be happy to help.
Ready to get started?
Request a no-risk 14-day free trial to see how you can create a sticky compliance-as-a-service offering with Apptega.
.svg)

.webp)