Mastering ISO 27001: The Definitive Guide to Achieving Compliance
Learn everything about ISO 27001, understand who needs it, and get actionable tips to obtain your certification.

A surge in cyber-attacks. High-profile data breaches. Increased regulatory pressure. The era of remote work. The list goes on...
There are multiple factors contributing to an increased concern about cybersecurity and data protection in recent years. That’s why over 40,000 companies worldwide already align with ISO 27001, a leading international standard for information security management.
Most popular among sectors like finance, healthcare, technology, and government due to their sensitivity to data security and regulatory requirements, obtaining an ISO 27001 certification is good practice for companies of any size and kind.
In this guide, you'll learn about:
- The key requirements of ISO 27001, organizational context, leadership responsibilities, and planning for an ISMS.
- Annex A controls and how to implement the four ISO 27001:2022 control sets with practical examples.
- The step-by-step process to achieve compliance, including tips on using compliance automation software like Apptega.
- How to prepare for an ISO 27001 audit, with a comprehensive checklist to ensure readiness.
- How ISO 27001 and SOC 2 compare, highlighting key differences and helping you choose the right framework for your business.
By the end, you'll have a thorough understanding of the fundamentals and practical implementation of ISO 27001, ensuring your organization—or clients—can achieve continuous compliance with this essential framework.
.webp)
What is ISO 27001?
ISO 27001 is a cybersecurity framework for structuring how you establish, implement, and sustain your Information Security Management System (ISMS).
It provides a systematic and comprehensive approach to effectively managing information security risks and complying with applicable laws and regulations with the goal of protecting the three key aspects of information security: Confidentiality, integrity, and availability of data.
A key feature of ISO 27001 requirements is their flexibility. Any organization can adopt and adapt them to their own needs, which makes it suitable for small businesses, large enterprises, and everything in between.
Furthermore, ISO 27001 promotes a risk-based approach to information security, encouraging organizations to identify their specific risks and implement appropriate controls to mitigate them. This proactive stance not only prevents security breaches but also ensures that organizations can quickly respond to any incidents.
The standard also has a focus on continuous improvement, requiring regular reviews and updates to the ISMS to address evolving threats and business changes.
Understanding the ISO 27000 Family of Standards
ISO/EIC 27000 consists of a series of information security standards organizations can use to develop an information security management program. This set of standards outlines information security management systems, also known as ISMS, and related technologies and security practices you can implement to keep protected and sensitive data safe. This can be a variety of data, from your organization’s and client’s financial information to intellectual property and employee information. You can use ISO 27000 standards to decrease your cyber risks and implement plans to improve your security practices over time.
ISO 27000 has almost 50 individual standards, including ISO 27001, which we’re detailing within this resource center. You can think of ISO 27001 as an introduction to the ISO 27000 series, where you can garner more information about how the ISO standards create a framework to help you create and operate your ISMS. Specifically, ISO 27001 provides an overview of all of the controls, policies, and procedures you can implement to build your ISMS program and proceed toward an ISO 27001 certification, with emphasis on specific keywords and their related definitions.
Benefits of Aligning with ISO 27001
By adopting ISO 27001 controls, organizations can lower their risk profile and demonstrate their commitment to maintaining a secure environment for their information assets.
This leads to multiple positive outcomes, including:

Having an ISO 27001 certification helps in aligning with the requirements of various national and international regulations and standards, such as GDPR, HIPAA, and other data protection laws. By taking a few supplementary actions and implementing additional controls tailored to each regulation, you can easily pass your audit and achieve compliance with those frameworks.

Demonstrating ISO 27001 compliance signals customers and stakeholders that your organization takes information security seriously. This trust usually leads to more fruitful business relationships and enhances customer loyalty.

Ever thought of cybersecurity as a competitive edge? It may not be the first thing your marketing team highlights in their campaigns but it’s a crucial differentiator when done right.
A strong commitment to cybersecurity serves as a mark of excellence, becoming a key factor for clients and partners in selecting service providers. Moreover, it can play an important role in retaining top talent, which contributes to the stability of your company.

The structured approach of ISO 27001 promotes streamlined processes within an organization. This can lead to improved operational efficiency and reduced costs associated with managing information security.
Overall, building robust and efficient cybersecurity programs by combining popular standards like ISO 27001 with compliance automation software leads to significant cost savings and unlocks tons of business opportunities.
Check this ROI calculator to see these potential benefits using your own numbers.
Key Requirements of ISO 27001
In general, ISO 27001 is not a mandatory certification. However, some industries require it as part of contractual or other legal obligations.
While it may not be mandatory for your organization to become ISO 27001 certified, it can bring a number of benefits to your security posture, especially if you’re just starting out building an information security program or if you’re looking for ways to identify gaps in your existing processes and mature your program as your organization scales.
To become ISO 27001 certified, you will need to complete a successful ISO 27001 audit. This process will include a review of your organization’s information security policies, implemented practices, and security infrastructure.
More specifically, these are the seven ISO 27001 requirements for your ISMS:
- Context of the Organization:
You need to understand your organization’s context, including internal and external issues that can affect its information security objectives. Identify interested parties and their requirements regarding information security.
- Leadership:
Top management must demonstrate leadership and commitment to the ISMS. This includes establishing an information security policy that’s been approved by your executive leadership (and/or board as appropriate), assigning roles and responsibilities, and ensuring that the ISMS objectives align with the organization’s strategic direction.
- Planning:
You need to establish and maintain risk management processes to identify, assess, and treat information security risks. Develop a risk treatment plan and set measurable information security objectives.
- Support:
Ensure all necessary resources for the ISMS. These include the competence of personnel, promoting awareness, and establishing effective communication. You also need to maintain documented information as required.
- Operation:
This implies implementing and managing the processes needed to meet information security objectives. This includes implementing risk treatment plans and managing changes in a controlled manner.
- Performance Evaluation:
You must continuously monitor, measure, analyze, and evaluate the performance of the ISMS. You also shall conduct internal audits at planned intervals to ensure conformity to the standard, which means you should establish a continuous compliance program. Perform management reviews to assess the effectiveness of the ISMS.
- Improvement:
You need to address nonconformities and take corrective actions to continually improve the ISMS. This includes making necessary updates to policies, procedures, and controls to adapt to changing threats and business needs.
Annex A Controls:
Lastly, you need to implement applicable controls from Annex A, which includes 93 controls organized into four categories: Organizational Controls, People Controls, Physical Controls, and Technological Controls. These controls help mitigate identified risks and enhance information security across the organization. We’ll go over these controls in more detail in the following section.
By meeting the above requirements, you can establish a robust Information Security Management System that not only protects your information assets but also enhances your overall security posture and compliance readiness.
Want to accelerate your ISO 27001 compliance process?
With Apptega’s ISO 27001 compliance software, you can use streamlined questionnaires, integrations to your sources of truth, and framework crosswalking to run through ISO 27001 assessment and audit like a breeze.
What Are the ISO 27001 Controls?
When talking about ISO 27001 controls, we will focus on Annex A of the latest version of the framework, ISO 27001:2022.
This updated standard introduced a revised and more streamlined set of controls, reducing the total number from 114 to 93 and reorganizing them into four main categories while including 11 new controls to address emerging security trends and technologies.
Here’s a detailed view of the four control sets and its specific controls:
1. Organizational Controls
These controls focus on the broader organizational framework for information security.
- A.5.1 Information security policies: Policies for information security
- A.5.2 Review of the policies for information security: Regular review and update of policies
- A.5.3 Information security roles and responsibilities: Define and communicate roles
- A.5.4 Segregation of duties: Minimize risk by separating responsibilities
- A.5.5 Contact with authorities: Maintain contact with relevant authorities
- A.5.6 Contact with special interest groups: Collaborate with external parties
- A.5.7 Threat intelligence: Use threat intelligence to improve security posture
- A.5.8 Information security in project management: Integrate security in project management
- A.5.9 Inventory of information and other associated assets: Maintain an inventory
- A.5.10 Acceptable use of information and other associated assets: Define acceptable use
- A.5.11 Return of assets: Ensure proper return of assets
- A.5.12 Classification of information: Classify information based on sensitivity
- A.5.13 Labeling of information: Proper labeling of classified information
- A.5.14 Management of removable media: Control removable media usage
- A.5.15 Disposal of media: Secure disposal of media
- A.5.16 Physical and environmental security: Protect physical assets
- A.5.17 Work from home: Implement security measures for remote work
- A.5.18 Clear desk and clear screen policy: Ensure desks and screens are clear
- A.5.19 Information transfer: Secure information transfer
- A.5.20 Access control: Control access to information systems
- A.5.21 User access management: Manage user access rights
- A.5.22 System and application access control: Secure system access
- A.5.23 Use of cryptography: Implement cryptographic controls
- A.5.24 Security of network services: Ensure network service security
- A.5.25 Monitoring of system use: Monitor systems for security breaches
- A.5.26 Information security in supplier relationships: Manage supplier security
- A.5.27 Incident management: Manage and respond to security incidents
- A.5.28 Security improvement: Continually improve security measures
- A.5.29 Compliance with legal and contractual requirements: Ensure compliance
- A.5.30 Information security review: Regularly review security measures
- A.5.31 Independent review of information security: External audits
- A.5.32 Secure development: Secure software development practices
- A.5.33 Security requirements of information systems: Define security requirements
- A.5.34 Security in development and support processes: Integrate security in development
- A.5.35 Test data: Manage test data securely
- A.5.36 Monitoring and review of supplier services: Monitor supplier security
- A.5.37 Outsourced development: Secure outsourced development
2. People Controls
These controls emphasize the role of human resources in information security.
- A.6.1 Screening: Screen potential employees for security risks
- A.6.2 Terms and conditions of employment: Include security responsibilities
- A.6.3 Awareness, education, and training: Educate staff on security
- A.6.4 Disciplinary process: Address security breaches
- A.6.5 Responsibilities after termination or change of employment: Manage departing employees
- A.6.6 Contact with authorities: Maintain contact with legal authorities
- A.6.7 Contact with special interest groups: Engage with security communities
- A.6.8 Information security in project management: Integrate security in projects
3. Physical Controls
These controls focus on securing the physical aspects of information security.
- A.7.1 Physical and environmental security: Protect physical premises
- A.7.2 Equipment security: Secure hardware and equipment
- A.7.3 Secure areas: Restrict access to secure areas
- A.7.4 Security of assets off-premises: Protect off-site assets
- A.7.5 Secure disposal or reuse of equipment: Manage disposal of hardware
- A.7.6 Clear desk and clear screen policy: Maintain clean workspaces
- A.7.7 Equipment maintenance: Regularly maintain equipment
- A.7.8 Removal of assets: Control asset removal
- A.7.9 Access control: Control physical access to buildings
- A.7.10 Protection against environmental threats: Protect against environmental risks
- A.7.11 Working in secure areas: Control activities in secure areas
- A.7.12 Maintenance of security equipment: Maintain security devices
- A.7.13 Secure disposal of media: Securely dispose of media
- A.7.14 Physical security monitoring: Monitor physical security
4. Technological Controls
These controls address the technological aspects of securing information.
- A.8.1 Use of cryptography: Implement cryptographic controls
- A.8.2 Security of network services: Ensure secure network services
- A.8.3 Monitoring of system use: Monitor systems for security breaches
- A.8.4 Information security in supplier relationships: Secure supplier interactions
- A.8.5 Incident management: Manage and respond to security incidents
- A.8.6 Security improvement: Continuously improve security measures
- A.8.7 Compliance with legal and contractual requirements: Ensure compliance
- A.8.8 Information security review: Regularly review security measures
- A.8.9 Independent review of information security: External audits
- A.8.10 Secure development: Ensure secure software development
- A.8.11 Security requirements of information systems: Define security requirements
- A.8.12 Security in development and support processes: Integrate security in development
- A.8.13 Test data: Secure test data management
- A.8.14 Monitoring and review of supplier services: Monitor supplier security
- A.8.15 Outsourced development: Secure outsourced development
- A.8.16 Configuration management: Manage system configurations
- A.8.17 Information deletion: Secure deletion of information
- A.8.18 Data masking: Implement data masking techniques
- A.8.19 Data leakage prevention: Prevent data leaks
- A.8.20 Monitoring activities: Monitor security activities
- A.8.21 Web filtering: Implement web filtering controls
- A.8.22 Secure coding: Ensure secure coding practices
Implementing these controls requires a systematic approach, which starts with understanding the requirements, assessing your organization’s risk profile, and then selecting the appropriate ISO 27001 controls to tackle.
You may, for example, address access control by setting up procedures for granting access to systems that include multi-factor authentication or biometrics. For cryptography, you may adopt specific mechanisms that make it difficult, even after a systems breach, for anyone to read and understand your data. For the business continuity control, you might want to set up redundancies and failover mechanisms that allow your organization to maintain essential functions in the case of a cyberattack, infrastructure failure, or natural disaster.
A key step of implementation of these controls is documentation, training, and ongoing monitoring so that your organization can continuously improve.
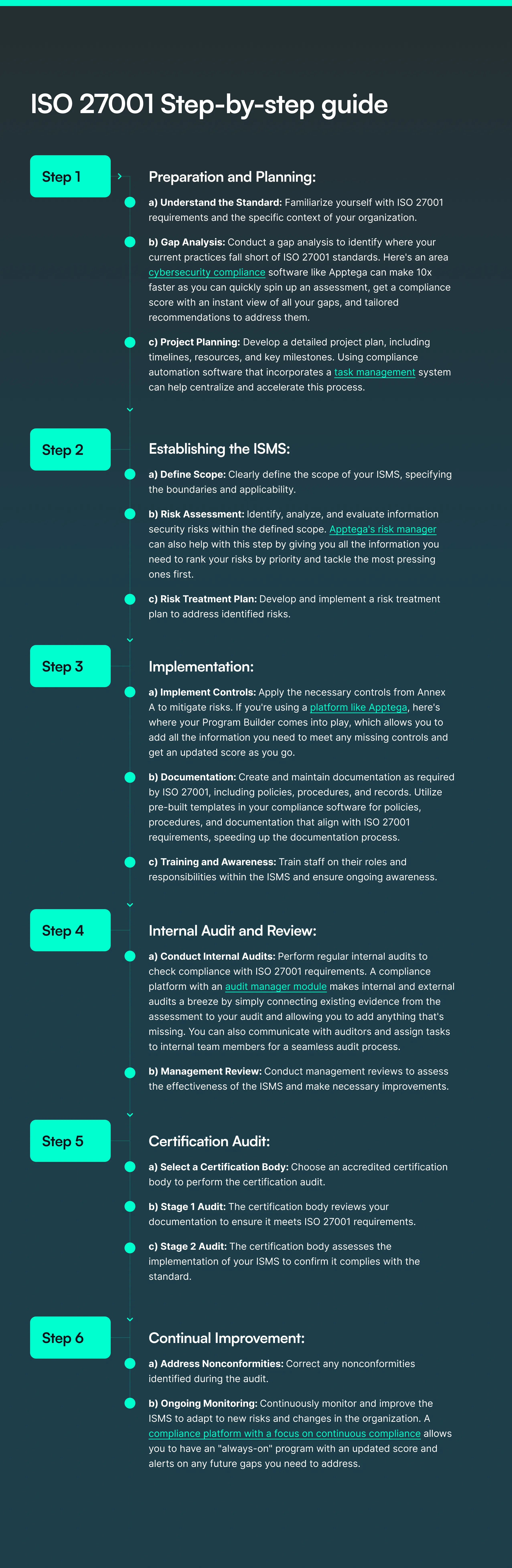
Achieving ISO 27001 Compliance: A Step-by-Step Guide
Achieving ISO 27001 compliance involves several stages, from initial preparation to maintaining compliance.
This section provides a detailed breakdown of the ISO 27001 compliance process, explains how to leverage compliance automation software like Apptega for embarking in a continuous compliance journey, and shares best practices for maintaining ISO 27001 compliance.
Preparation and Planning
- Understand the Standard: Familiarize yourself with ISO 27001 requirements and the specific context of your organization.
- Gap Analysis: Conduct a gap analysis to identify where your current practices fall short of ISO 27001 standards. Here’s an area cybersecurity compliance software like Apptega can make 10x faster as you can quickly spin up an assessment, get a compliance score with an instant view of all your gaps, and tailored recommendations to address them.
- Project Planning: Develop a detailed project plan, including timelines, resources, and key milestones. Using compliance automation software that incorporates a task management system can help centralize and accelerate this process.
Establishing the ISMS
- Define Scope: Clearly define the scope of your ISMS, specifying the boundaries and applicability.
- Risk Assessment: Identify, analyze, and evaluate information security risks within the defined scope. Apptega’s risk manager can also help with this step by giving you all the information you need to rank your risks by priority and tackle the most pressing ones first.
- Risk Treatment Plan: Develop and implement a risk treatment plan to address identified risks.
Implementation
- Implement Controls: Apply the necessary controls from Annex A to mitigate risks. If you’re using a platform like Apptega, here’s where your Program Builder comes into play, which allows you to add all the information you need to meet any missing controls and get an updated score as you go.
- Documentation: Create and maintain documentation as required by ISO 27001, including policies, procedures, and records. Utilize pre-built templates in your compliance software for policies, procedures, and documentation that align with ISO 27001 requirements, speeding up the documentation process.
- Training and Awareness: Train staff on their roles and responsibilities within the ISMS and ensure ongoing awareness.
Internal Audit and Review
- Conduct Internal Audits: Perform regular internal audits to check compliance with ISO 27001 requirements. A compliance platform with an audit manager module makes internal and external audits a breeze by simply connecting existing evidence from the assessment to your audit and allowing you to add anything that’s missing. You can also communicate with auditors and assign tasks to internal team members for a seamless audit process.
- Management Review: Conduct management reviews to assess the effectiveness of the ISMS and make necessary improvements.
Certification Audit
- Select a Certification Body: Choose an accredited certification body to perform the certification audit.
- Stage 1 Audit: The certification body reviews your documentation to ensure it meets ISO 27001 requirements.
- Stage 2 Audit: The certification body assesses the implementation of your ISMS to confirm it complies with the standard.
Continual Improvement
- Address Nonconformities: Correct any nonconformities identified during the audit.
- Ongoing Monitoring: Continuously monitor and improve the ISMS to adapt to new risks and changes in the organization. A compliance platform with a focus on continuous compliance allows you to have an “always-on” program with an updated score and alerts on any future gaps you need to address.
If you follow these steps and leverage automation tools like Apptega, your organization or clients can achieve and maintain ISO 27001 compliance, ensuring robust information security management and continuous improvement.
For MSSPs and other security providers specifically, using a tool like Apptega facilitates building your ISO 27001 compliance management services on an automated platform that fosters efficiency and continuous monitoring for stickier client relationships (vs simple one-off assessments), reduced internal burden, higher margins, and increased recurrent revenue. Check out our partner program to see how we make this possible, and how we win together.
For a more detailed explanation on how you can use Apptega to streamline ISO 27001 compliance, watch this 2-minute demo video:
Preparing for an ISO 27001 Audit
Achieving ISO 27001 certification involves undergoing a rigorous audit process that typically has two main stages:

The auditor reviews your organization's documentation to ensure it aligns with ISO 27001 requirements. This includes your ISMS scope, risk assessment, risk treatment plan, policies, procedures, and other relevant documents.
The auditor identifies any gaps or nonconformities in your documentation and provides feedback on areas that need improvement before proceeding to the next stage.

The auditor evaluates the implementation and effectiveness of your ISMS. This involves on-site inspections, interviews with staff, and evidence gathering to verify that your organization's practices conform to the documented ISMS.
If the auditor determines that you are meeting all ISO 27001 standards, you’ll get your ISO 27001 certification.
Throughout both stages, auditors will look for evidence that your organization has implemented the necessary controls and that these controls are functioning as intended.
That’s why managing the entire process with audit management software can result in a smoother and faster process as you’ll have all documentation, task management, and back and forth communication with your auditor in one place.
To ensure the ISO 27001 audit process goes smoothly, start by making sure all your documentation is up-to-date and accurate. This includes your ISMS scope, policies, procedures, risk assessments, and treatment plans. Good documentation shows your commitment to information security management and gives auditors a clear picture of your processes.
As covered earlier, you may also conduct regular internal audits to catch any issues before the official audit. These internal checks help you spot gaps and show auditors that you’re proactive about continual improvement. You must document all findings and the actions you’ve taken to address them. This not only keeps you organized but also proves that you’re constantly improving your ISMS.
It’s also crucial to get top management involved. Their active participation in ISMS reviews and decision-making shows a company-wide commitment to information security. This alignment ensures that the ISMS supports your strategic goals and integrates into your overall business processes.
Training your staff in their ISMS roles is equally vital. This helps everyone understand their responsibilities and the importance of information security. Employees should be prepared to discuss their roles and contributions during the audit, demonstrating a well-informed team. In fact, you should prepare your team for audit interviews so relevant employees can explain their roles and provide evidence of compliance with ISMS procedures.
A key component of the audit is to gather and organize evidence that shows how your ISMS controls are implemented and effective. This includes logs, reports, meeting minutes, training records, and incident response records. Having this evidence ready makes the audit process smoother and shows that your ISMS is operational and continuously monitored.
By following these steps, using the right software, and staying well-prepared, you can navigate the ISO 27001 audit process confidently and achieve your certification fast and smoothly.
ISO 27001 Checklist
In this guide, we’ve already covered most of the steps and requirements that are essential to get your ISO 27001 certification, but a detailed checklist is alway a great resource to ensure that you cover all necessary steps.
Use this simplified checklist to gauge your readiness and streamline your path to certification.
1. Initial Preparation
- Understand ISO 27001 Requirements: Familiarize yourself with the ISO 27001 standard and its requirements.
- Scope Definition: Clearly define the scope of your ISMS. Determine the boundaries and applicability, including departments, locations, and assets.
- Gap Analysis: Conduct a gap analysis to identify areas where your current practices do not meet ISO 27001 requirements. Create a remediation plan to meet any missing controls.
2. Documentation
- Information Security Policy: If you haven’t already, develop and document an information security policy that outlines your organization’s approach to managing information security.
- Risk Assessment Procedure: Create a procedure for conducting risk assessments, including methodologies, criteria for risk evaluation, and risk acceptance.
- Risk Treatment Plan: Document a risk treatment plan detailing how identified risks will be managed, mitigated, or accepted.
- ISMS Procedures and Controls: Develop and document procedures for all necessary controls, as specified in Annex A of ISO 27001.
- Statement of Applicability (SoA): Prepare a Statement of Applicability that lists the controls selected from Annex A and provides justification for their inclusion or exclusion.
3. Implementation
- Implement Controls: Implement the necessary controls across the organization. This includes technical, physical, and administrative controls.
- Training and Awareness: Conduct training sessions and awareness programs to ensure all employees understand their roles and responsibilities in the ISMS.
- Asset Management: Maintain an up-to-date inventory of information assets and implement appropriate classification and handling procedures.
4. Monitoring and Review
- Internal Audits: Schedule and perform regular internal audits to check the effectiveness of the ISMS and ensure compliance with ISO 27001 requirements.
- Management Review: Conduct regular management reviews to assess the performance of the ISMS, discuss audit findings, and decide on necessary improvements.
- Corrective Actions: Identify and implement corrective actions for any nonconformities or areas for improvement discovered during internal audits or management reviews.
5. Preparing for Certification
- Select a Certification Body: Choose an accredited certification body to conduct the ISO 27001 audit.
- Pass your Audit: Prepare for the Sstages 1 and 2 of the audit, where the certification body reviews your documentation and evaluates the implementation and effectiveness of your ISMS to ensure it meets ISO 27001 requirements.
6. Continuous Improvement
- Ongoing Monitoring: Continuously monitor and assess the ISMS to identify new risks and areas for improvement.
- Incident Management: Develop and test an incident response plan to handle security breaches effectively.
- Regular Updates: Regularly update documentation, procedures, and controls to reflect changes in the organization and emerging security threats.
ISO 27001 vs SOC 2: Key Differences and Similarities
ISO 27001 and SOC 2 are both standards designed to help organizations manage and protect their information security systems. However, they have different focuses, scopes, and requirements. By understanding these differences and similarities, you can choose the right framework for your needs.
If you consider aligning with both frameworks, using a solution like Apptega to crosswalk shared controls can avoid duplicating efforts and achieve compliance much faster.
- Scope and focus: ISO 27001 focuses on creating and maintaining an effective ISMS. SOC 2 is focused on security issues around data processed by service providers.
- Proving compliance: ISO 27001 compliance is documented by accredited bodies that certify requirements via an audit process. SOC 2 results in an attestation report rather than a certification. This report is prepared by an independent CPA firm and details the effectiveness of the organization’s controls based on the Trust Service Criteria.
- Applicability: ISO 27001 was designed for any type and size of organization. SOC 2 applies to organizations such as cloud service providers, SaaS companies, and data centers.
- Geographical relevance: ISO 27001 is globally recognized, making it suitable for organizations with international operations. Conversely, SOC 2 is predominantly used in the United States and is often required by American clients and partners.
ISO 27001 and SOC 2 are effective risk management frameworks emphasizing continuous improvement. Both provide third-party assurance of your commitment to protecting data. The processes and controls for ISO 27001 can often overlap with SOC 2 requirements. By strategically aligning the implementation of both standards, organizations can efficiently use their resources and streamline their compliance efforts.
Conclusion
As you think of embarking on the ISO 27001 journey, use this guide as a roadmap to navigate the compliance process. Obtaining your ISO 27001 certification is a significant milestone that showcases your commitment to information security.
With the right approach and resources, your organization or clients can successfully achieve and maintain compliance, ensuring robust protection against security threats. This will result in reduced risk, lower cyber insurance premiums, new business opportunities, and zero operational disruptions.
ISO 27001 FAQs
ISO/EIC 27001 is a joint effort between the International Organization for Standardization (ISO) and the International Electrotechnical Commission (EIC). The organizations released the first set of standards in 2005 and then updated and issued revisions in 2013 and again in 2022. ISO/IEC 27001:2022 is the most current version. While ISO/EIC sets the standards, they do not manage compliance audits, which external auditors handle for certification.
ISO 27001 can help your organization develop, manage, and mature your information security management program. Some industries require ISO certification as part of regulatory or other compliance requirements; however, even if your organization isn’t required to attest to ISO 27001 standards, adopting these measures can help build confidence with your clients, partners, vendors, key stakeholders, and general public that your organization takes information security seriously and that you’ve implemented internationally recognized standards to keep your data safe.
ISMS is an abbreviation for information security management system. An information security management system is a documented system your organization can use to ensure you’ve implemented necessary (and required) measures to protect information within your organization and shared with third-parties. This includes your security standards and related controls used to create, implement, and manage your information security practices.
An ISMS is important because it can help your organization more effectively protect your systems and processes from unauthorized access to sensitive and protected data. It can help you identify critical weaknesses and vulnerabilities, and establishes plans and processes to mitigate cyber risks and improve your overall cybersecurity posture. An ISMS outlines systematic and repeatable processes you can use to help keep your data safe and better protect your organization from cyber risks.
The most current version of ISO 27001 is ISO/EIC 27001: 2022. Find out more about ISO 27001, including where and how you can get a copy, at: https://www.iso.org/standard/27001.
Core compliance requirements include demonstrating effective organizational context, leadership, planning, support, operation, performance evaluation and improvement. For version 2022, your organization will also have to submit an SoA with specific information about the controls you implemented and those you have not?
There are 114 controls organized into 14 sections for ISO 27001: 2013: information security policies (2 controls), organization of information security (7 controls), human resource security (6 controls), asset management (6 controls), access control (14 controls), cryptography (2 controls), physical and environmental security (15 controls), operations security (14 controls), communications security (7 controls), system acquisition, development and maintenance (13 controls), supplier relationships (5 controls), information security incident management (7 controls), information security aspects of business continuity management (4 controls), and compliance (8 controls). For more information, check out the controls section in this resource center.
There are 93 controls spanning four control sets for version 2022: organization, people, physical, and technologies.
ISO 27001 and ISO 27002 work together, but they are different. ISO 27001 is the official standard that outlines all of the controls, policies, and procedures for ISO certification. ISO 27002 outlines all of the sub-controls you can implement to meet requirements defined in each ISO 27001 control.
ISO 27001 and NIST 800-53 are different, but share similarities. Both can be used as frameworks to build your cybersecurity program. ISO 27001 deals specifically with information security management systems, while NIST 800-53 guides security practices specifically for federal information systems. ISO 27001 is generally less technical than NIST 800-53, with more focus on risk reduction for ISO 27001.
Still have a question?
Get in touch with us and we would be happy to help.
Ready to get started?
Request a no-risk 14-day free trial to see how you can create a sticky compliance-as-a-service offering with Apptega.
.svg)






